[ad_1]
In a nutshell: Google detailed how North Korean hackers mounted a sophisticated social engineering campaign to infect cybersecurity researchers with malware. The campaign included numerous social media accounts and even a research “blog” created to build credibility. Some researchers were infected using Visual Studio files embedded with malware, while others were infected by merely visiting a website.
According to Google’s Threat Analysis Group, state-sponsored North Korean hackers are targeting security researchers via social engineering. Writing in a blog post, the group says that the campaign specifically targeted researchers working on vulnerability research and development. The campaign has been going for the “past several months.”
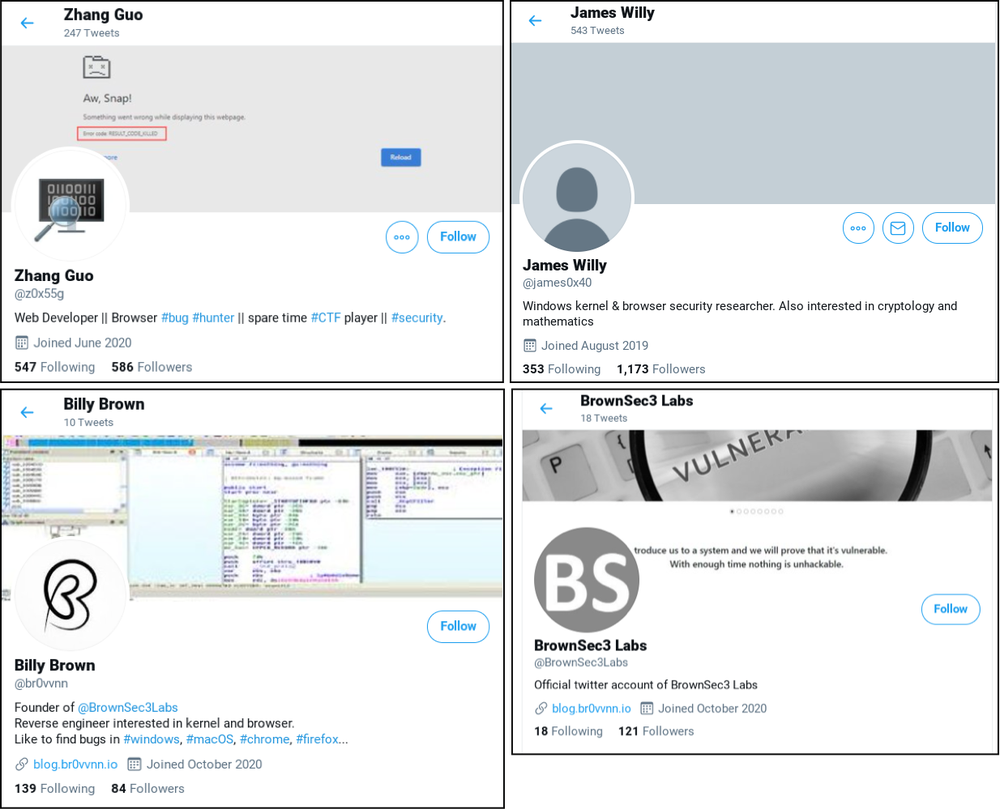
The hackers attempted to establish a rapport with the security research community by creating a blog and several Twitter accounts. The blog itself featured write-ups of previously discovered vulnerabilities and “guests posts” with legitimate security researchers on the bylines. The various Twitter accounts would post links to their blog, retweet the other posts, and link to YouTube videos of alleged exploits. Google says this was likely an attempt to build credibility with other researchers.
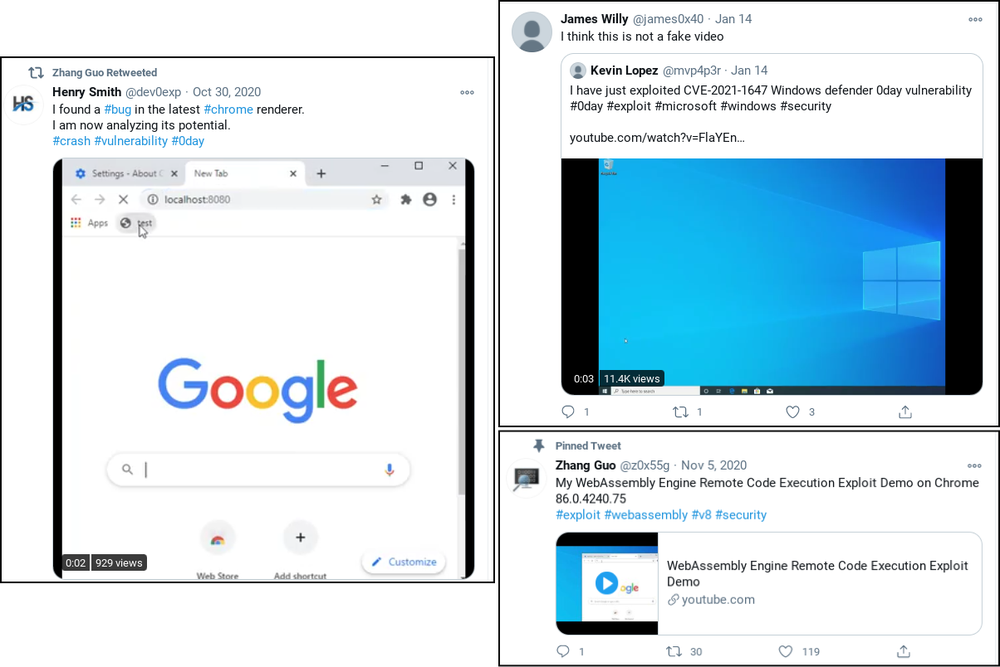
One YouTube video claimed to exploit CVE-2021-1647, an actual Windows Defender vulnerability that Microsoft recently patched. However, Google (along with eagle-eyed YouTube commenters) noticed that the video was fake. The attackers attempted to double down on their exploit claims by retweeting the video using another Twitter account, stating that “I think this is not a fake video.”
Once the hackers establish communications with a security researcher, they invite the person to collaborate on some “research.” The attackers then send the target a Visual Studio Project file embedded with malware. Upon opening the file, the malicious program establishes a connection back to the hackers.
Even scarier, Google confirmed that some researchers were infected by merely visiting the hackers’ blog. A fully patched Windows 10 system and up to date Chrome browser did not stop the infection. Unfortunately, Google could not verify exactly how the researchers’ fully updated systems were infected other than they all clicked on a link to a blog that surreptitiously installed a malicious service. This service creates an in-memory backdoor to a command and control server.
The attackers used multiple social media platforms to target security researchers, including Twitter, LinkedIn, Telegram, Discord, and Keybase. Google helpfully listed every known account and domain used by the attackers. It is concerning because it shows that even experienced cybersecurity experts can be fooled by a sophisticated enough social engineering campaign. Anyone interested in security research should check out the full blog post to lessen their chances of becoming a target.
[ad_2]
Source link