[ad_1]
Facebook has published new findings that unveil two Palestinian organisations have been running cyberespionage campaigns against government officials, student groups, and security forces.
The two groups both used fake and compromised social media accounts posing primarily as young women, and also as Fatah or Hamas supporters, various military groups, journalists, and activists to build trust with people in order to trick them into installing malicious software.
According to Facebook, one group dubbed as Arid Viper has been linked to the cyber arm of Hamas. Meanwhile, the other is linked to the Palestinian Preventive Security Service (PSS), one of the security arms of Palestine, where the current president is a member of the Fatah party. Fatah and Hamas have been engaged in a civil war since 2006.
Publishing a threat report [PDF] of Arid Viper’s activity, Facebook said the threat actor used fully functional custom iOS surveillanceware that was capable of stealing sensitive user data from iPhones without requiring the devices to be jailbroken.
The surveillanceware, labelled as Phenakite, was trojanised inside fully functional chat applications that used the open-source RealtimeChat code for legitimate reasons. This malware could also direct victims to phishing pages for Facebook and iCloud in order to steal credentials for those services. As this process used legitimate developer certificates, iOS devices did not need to be jailbroken to be surveilled.
While Phenakite did not require a jailbreak for installation, once on a device, it needed to adhere to the usual operating system security controls that prevent access to sensitive information from unauthorised applications. To circumvent that, Phenakite came bundled with the publicly available Osiris jailbreak and the Sock Port exploit, which meant that Phenakite was capable of using Osiris to jailbreak all 64-bit devices on iOS 11.2 to 11.3.1 or the Sock Port exploit to extend this to devices running iOS 10.0 to 12.2
If the Osiris jailbreak was successful, Phenakite could then retrieve photos from the camera roll, take images with the device camera, retrieve contacts, silently record audio, access documents and text messages, and upload WhatsApp data.
The Android malware deployed by Arid Viper, meanwhile, required victims to install apps from third-party sources on their devices. The group used hundreds of attacker-controlled sites, along with the aforementioned fake social media accounts, to create the impression that the apps were legitimate in order to convince victims into installing them.
The trojanised chat applications in both Android and iOS were primarily pretending to be dating apps.
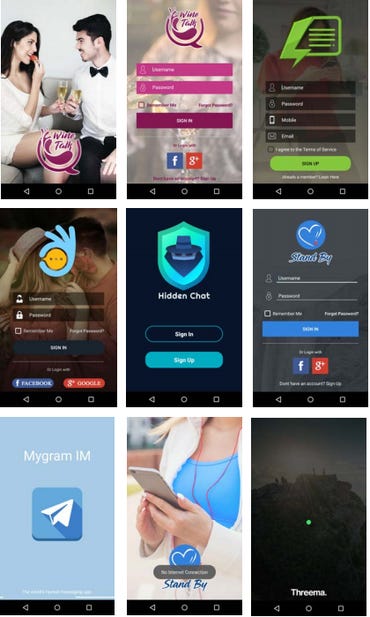
Examples of the trojanised chat applications.
Image: Facebook
In all instances, the successful installation of these tools did not require any exploits, which the report said suggests that Arid Viper operators heavily relied on social engineering to distribute their malware.
Of particular concern to Facebook was that Arid Viper’s use of custom surveillanceware demonstrated that this capability was becoming increasingly attainable by adversaries even if they are not as technologically sophisticated.
“As the technological sophistication of Arid Viper can be considered to be low to medium, this expansion in capability should signal to defenders that other low-tier adversaries may already possess, or can quickly develop, similar tooling,” Facebook said.
Meanwhile, PSS used similar tactics of utilising social engineering to coerce their targets into installing Android and Microsoft malware, Facebook said. PSS malware, once installed onto devices, collected information such as device metadata, call logs, location, contacts, and text messages. In rare cases, it also contained keylogger functionality.
Rather than targeting pro-Fatah individuals, the PSS used its malware to targets various groups, including people opposing the Fatah-led government, journalists, human rights activists, and military groups including the Syrian opposition and Iraqi military.
According to Facebook, these findings are the first public reporting of this particular cyberespionage activity conducted by PSS.
Following the investigation into the conduct of Arid Viper and PSS, Facebook has released a set of indicators addressing such activity. The indicators include 10 Android malware hashes, two iOS malware hashes, eight desktop malware hashes, and 179 domains.
Facebook has also notified targeted individuals and industry partners, which led to Arid Viper’s developer certificates being revoked and various accounts and websites being blocked or removed.
Last month, Facebook said it disrupted a network of hackers tied to China that were attempting to distribute malware via malicious links shared under fake personas. The malware allegedly targeted around 500 users.
Related Coverage
[ad_2]
Source link