[ad_1]
Cyberattacks against healthcare organizations have doubled during the coronavirus pandemic, research suggests.
On Wednesday, IBM released the company’s annual X-Force Threat Intelligence Index, which analyzed data from the previous year to track the evolution of new threats, malware development, and cyberattacks.
The 2021 index includes some notable trends, perhaps the most significant being how many threat actors pivoted their campaigns toward organizations involved in fighting the COVID-19 pandemic during 2020.
According to IBM researchers, attacks against organizations crucial to coronavirus research and treatment experienced double the ‘usual’ rate of attacks in 2020. These entities include hospitals, pharmaceutical manufacturers, medical companies, and energy firms involved in the COVID-19 supply chain.
IBM believes that this change in focus is due to cyberattackers banking on the fact that these organizations could not — and still cannot — afford any downtime that could impact COVID-19 programs. As a result, victims may be more likely to pay up, for example, when ransomware is deployed.
According to the tech giant, manufacturing and the energy sector were second only to finance and insurance when it comes to the most attacked industries worldwide last year. Of particular note, too, is a close to 50% increase in attacks exploiting vulnerabilities in industrial control systems (ICS).
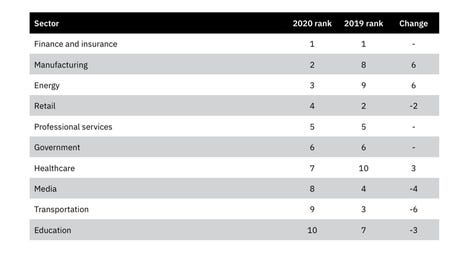
“In essence, the pandemic reshaped what is considered critical infrastructure today, and attackers took note. Many organizations were pushed to the front lines of response efforts for the first time — whether to support COVID-19 research, uphold vaccine and food supply chains, or produce personal protective equipment,” commented Nick Rossmann, Global Threat Intelligence Lead at IBM Security X-Force. “Attackers’ victimology shifted as the COVID-19 timeline of events unfolded, indicating yet again, the adaptability, resourcefulness, and persistence of cyber adversaries.”
Over the course of 2020, ransomware became the most popular attack method, claiming 23% of all incidents analyzed by IBM. Sodinokibi was the most prolific ransomware family in use, raking in a “conservative estimate” of at least $123 million in the past year for its operators — and with up to two-thirds of victims giving in, and paying up.
Double extortion, in which a victim organization’s systems are infected with ransomware, a blackmail payment is demanded, and attackers threaten to leak stolen data, is also becoming more popular.
The report also found a 40% increase in Linux-based malware families and a 500% surge in malware written in the Go programming language.
“Similar to hybrid cloud’s playbook to “write once, run anywhere,” attackers are using malware that can more easily run on various platforms, including cloud environments,” IBM added.
Other points of interest include:
- Collaboration tool spoofing: Many of the most spoofed brands over 2020 offer remote collaboration tools, including Google, Dropbox, and Microsoft.
- Open source: Threat actors are turning to open source malware more frequently than before, with APT28, APT29 and Carbanak among users.
- Cryptomining: Over 2020, there was a 13% increase in new code in Linux cryptocurrency mining malware.
- Scanning: Scan-and-exploit attack vectors were the most common way for threat actors to compromise a system last year, surpassing phishing for the first time in years.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link