[ad_1]
A hot potato: Microsoft says that 92% of Exchange servers have been patched or mitigated risks following four zero-day exploits. However, the company warns that already compromised servers are still at risk. Admins are advised to check their servers to ensure that secondary attacks such as ransomware attacks or data exfiltration are prevented from happening.
Microsoft explains that its one-click mitigation tool and recent update of Microsoft Defender have expanded the reach of server mitigation, resulting in some 92% of vulnerable Exchange servers worldwide having either been patched or mitigated. It’s positive news, but Microsoft highlights that patching isn’t going to protect already-compromised servers.
“Many of the compromised systems have not yet received a secondary action, such as human-operated ransomware attacks or data exfiltration, indicating attackers could be establishing and keeping their access for potential later actions.”
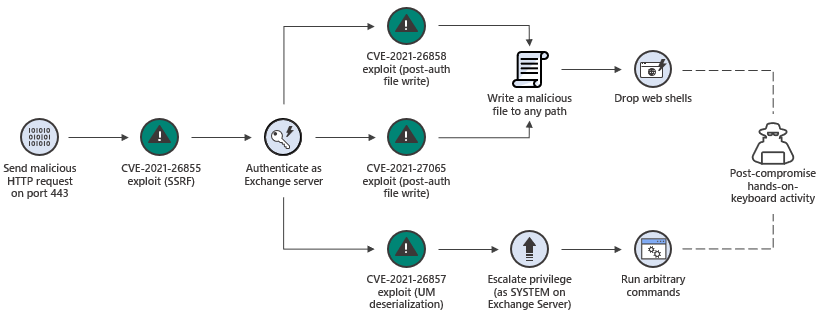
While patching safeguards your organization’s servers from an initial attack, admins are advised to monitor their systems to ensure they aren’t still vulnerable. This could involve a follow-on attack on an already-compromised server, or using stolen data to compromise other networks.
Microsoft has published guidance online for server admins to refer to, but the bottom line is clear: while the company’s software and online tools are helping to patch the vast majority of servers worldwide, it’s essential that admins check whether or not their organization’s Exchange servers have already been compromised. If so, ransomware or data exfiltration could follow at a later point in time.
[ad_2]
Source link